SOPHOS PHILIPPINES
Full disk encryption: the first line of defense
Central Device Encryption Features
Disk Encryption
Protect devices and data with full disk encryption for Windows and macOS, managed alongside our entire cybersecurity portfolio in Sophos Central.
Intuitive
Easy to setup, easy to manage. There’s no server to deploy and no need to configure back-end key servers. Start securing devices in minutes.
Compliance
With the increase in remote working, it is more important than ever to secure devices and data. Verify device encryption status and demonstrate compliance.
Self-service Portal
Reduce calls to the IT helpdesk. The self-service portal lets users regain access to their devices so they’re back up and running faster – and IT has one less ticket to deal with.
Secure File Share
Confidentially share sensitive files. A password protected HTML wrapper ensures only recipients with the correct password can access a document.
Visibility
Give admins visibility of devices across their estate. Simply ensure machines have been encrypted, or drill down into details about disks and encryption methods.
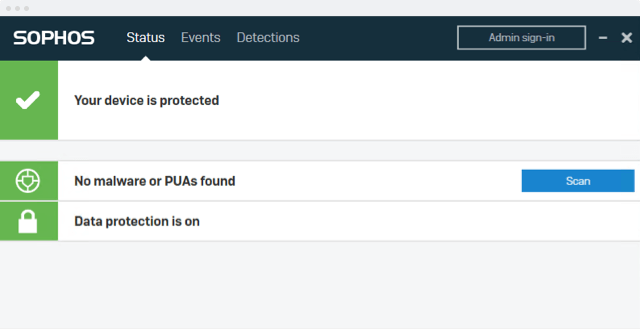
Disk Encryption
Increased remote working makes it more important than ever to secure computers and the data on them. With the huge number of laptops lost, stolen, or misplaced every day, a crucial first line of defense against the loss or theft of devices is full disk encryption. Sophos Central Device Encryption leverages Windows BitLocker and macOS FileVault to secure devices and data.
Intuitive
Part of the Sophos Central unified security console, Central Device Encryption is managed right alongside our entire range of market-leading protections. The web-based console means there’s no server to deploy and no need to configure back-end key servers. Central Device Encryption uses the same core agent as Intercept X, meaning existing Sophos customers have no additional agent to deploy and can start encrypting computers in minutes.
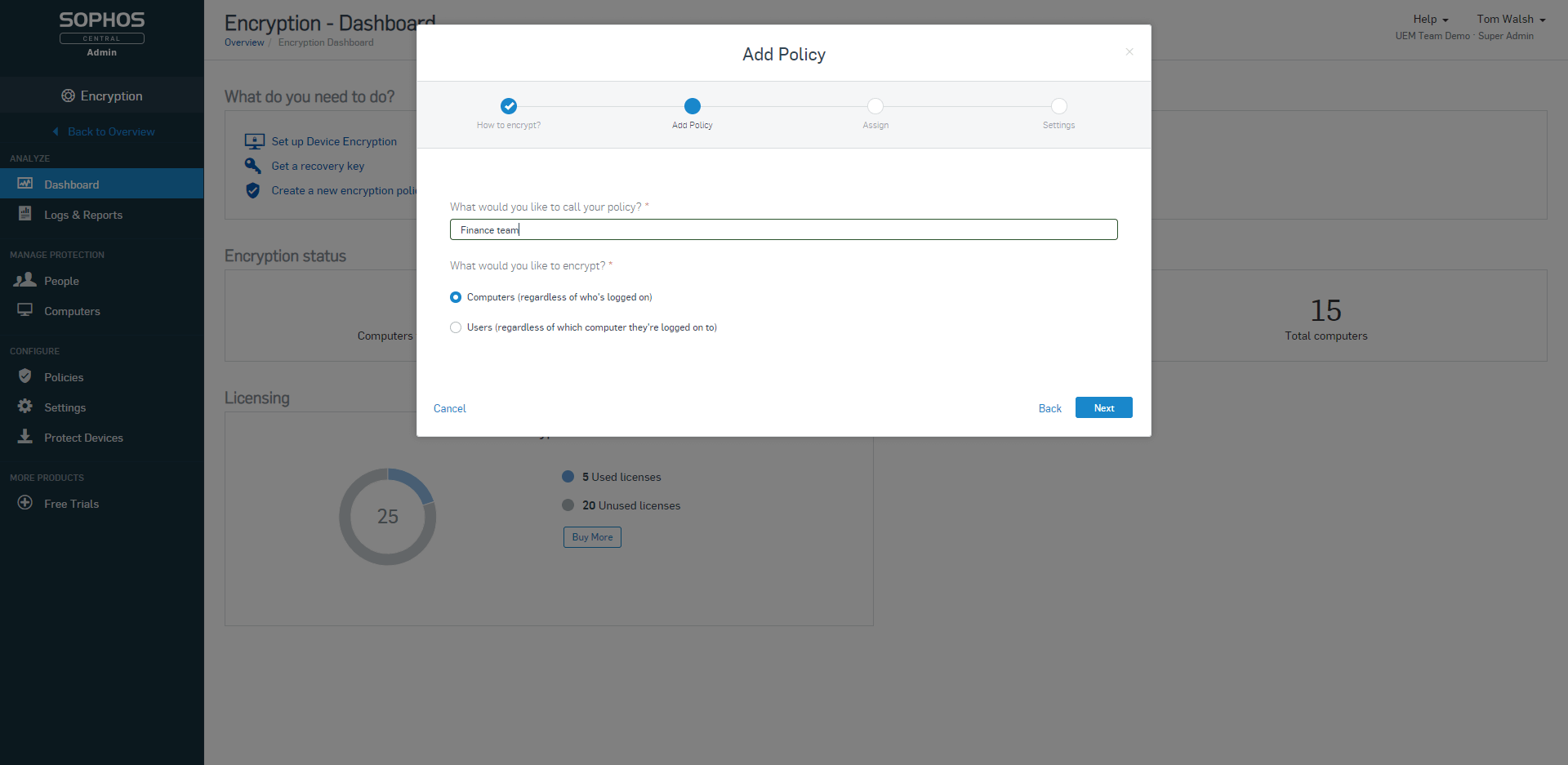
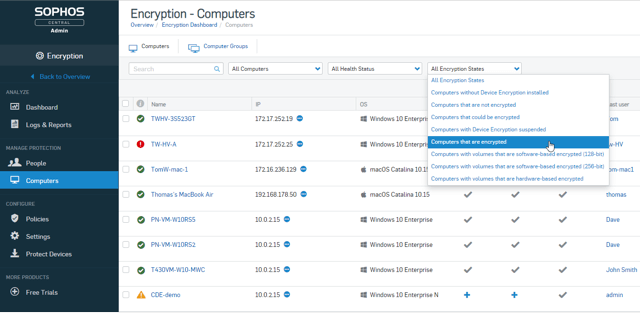
Compliance
As a part of compliance requirements, companies often need to verify which computers in the organization are encrypted. And in the case of lost or stolen laptops, they must provide proof these missing devices are encrypted. Central Device Encryption makes it easy to verify encryption status and demonstrate compliance.
Get in touch!
Have a question? Concern? Request? We’d love to hear from you. Connect with us through the following ways.
Address
WSI Corporate Center 1005 Metropolitan Avenue, Corner Kakarong, Makati, 1205 Metro Manila
Phone:
+63 2 8858 5555
Fax:
+63 2 8858 5511
Hours
8 a.m. to 5:30 p.m., Monday-Friday
Fill out this short form and a member of our team will get back to you within 24 hours
Head Office
1005 Metropolitan Ave, Corner Kakarong, Makati, 1205 Metro Manila
Cebu Office
2F Unit 202-204, GMC Innovation Center, M. J. Cuenco Ave, Brgy San Roque Cebu City 6000
Davao Office
Unit 11, Plug Holdings Bldg, 141 R. Castillo St, Agdao, Davao City, 8000 Davao del Sur


