Consistent, data-driven ratings
Gain an outside-in view of your security posture so you can take preventative action. Scoring is based on our trusted, transparent ratings methodology and data collected on millions of organizations.
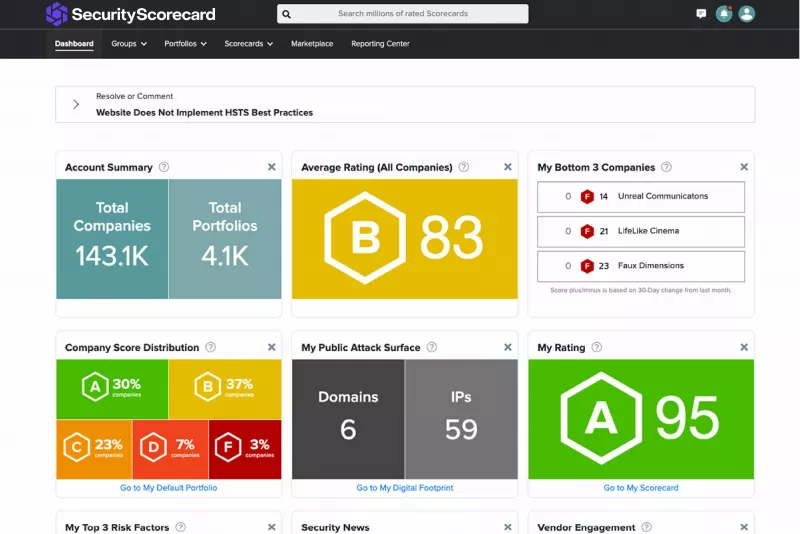
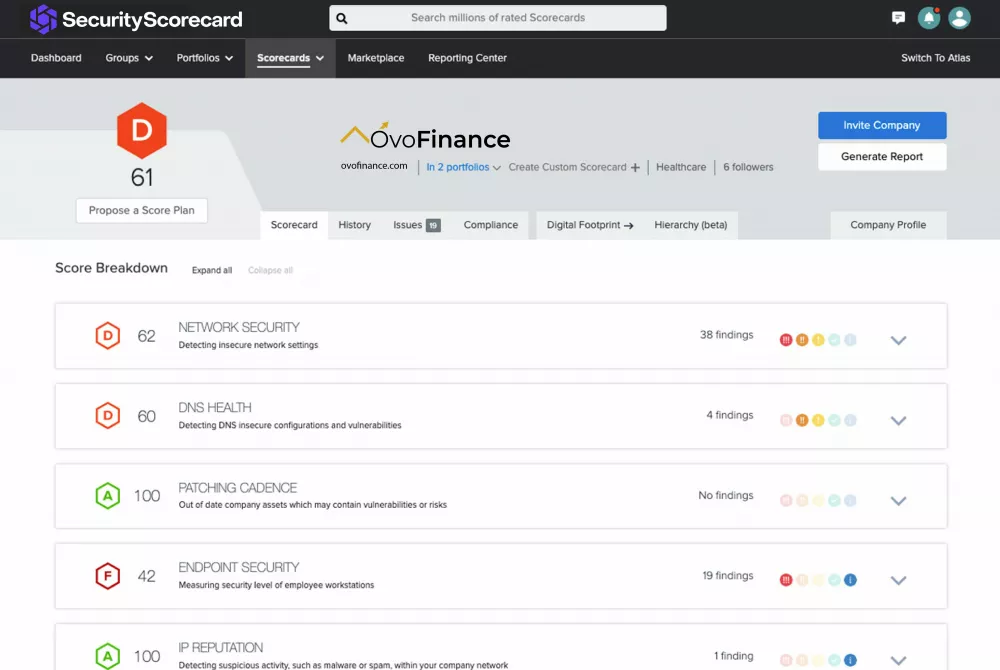
SecurityScorecard Ratings offer easy-to-read A-F ratings across ten groups of risk factors.
Network Security
The Network Security module checks public datasets for evidence of high risk or insecure open ports within the organization network.
DNS Health
The DNS Health module measures the health and configuration of an organization’s DNS settings. It validates that no malicious events occurred in the passive DNS history of the organization’s network.
Patching Cadence
The Patching Cadence module analyzes how quickly an organization installs security updates to measure vulnerability risk mitigation practices.
Endpoint Security
The Endpoint Security module tracks identification points that are extracted from metadata related to the operating system, web browser, and related active plugins.
IP Reputation
The IP Reputation and Malware Exposure module makes use of the SecurityScorecard sinkhole infrastructure as well as a blend of OSINT malware feeds and third-party threat intelligence data-sharing partnerships.
Application Security
The Application Security module uses incoming threat intelligence from known exploitable conditions identified via: whitehat CVE databases, blackhat exploit databases, and sensitive findings indexed by major search engines.
Cubit Score
The Cubit Score module measures a variety of security issues that an organization might have. For example, we check public threat intelligence databases for IP addresses that have been flagged.
Hacker Chatter
The Hacker Chatter module is an automated collection and aggregation system for the analysis of multiple streams of underground hacker chatter.
Information Leak
This Information Leak module makes use of chatter monitoring and deep web monitoring capabilities to identify compromised credentials being circulated by hackers.
Social Engineering
The Social Engineering Module is used to determine the potential susceptibility of an organization to a targeted social engineering attack.
“Because SecurityScorecard is a reputable, independent assessment source, Horizon Media can be more transparent with clients when it comes to reporting its cybersecurity rating.”

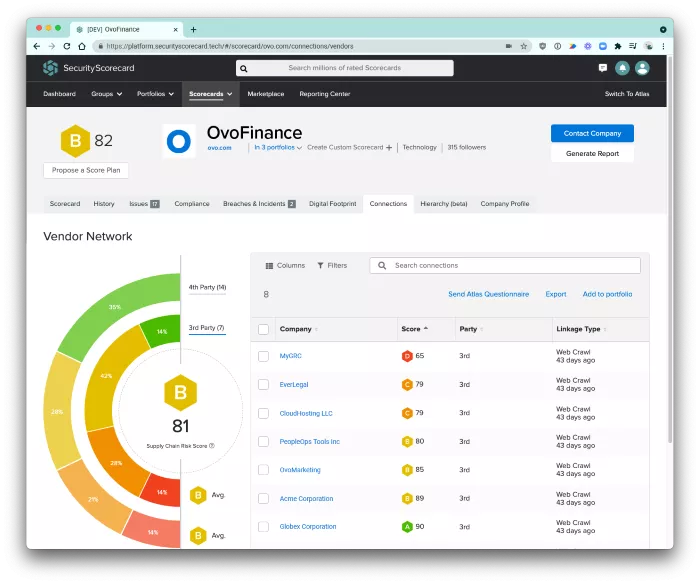
Instantly detect your Digital Supply Chain and your Supply Chain Risk Score
Gain a complete view of your vendor ecosystem, the security posture of each vendor, and a private Supply Chain Risk Score to understand the score of your entire ecosystem.
- Visualize your full vendor ecosystem: gain a ubiquitous view of cyber risk with unparalleled graphics giving you a full view of your ecosystem risk.
- Drive targeted discussions with your supply chain: pinpoint related risks and specific vulnerabilities within every vendor, so you can partner with your third parties to accelerate risk mitigation.
- Streamline vendor risk management workflows: simplify mitigation and quickly identify threat exposures with a single dashboard highlighting areas of strength and weakness across the full spectrum of vendors–including your fourth-party vendors.
What security ratings can do for you
Instantly rate, understand, and continuously monitor the security posture of any company worldwide. SecurityScorecard non-intrusively collects data from across the internet for an objective, outside-in perspective of an organization’s cybersecurity posture.
Identify and remediate the most critical areas of risk for your organization. SecurityScorecard Ratings offer easy-to-read A-F ratings across ten groups of risk factors, including DNS health, IP reputation, web application security, network security, leaked information, hacker chatter, endpoint security, and patching cadence.
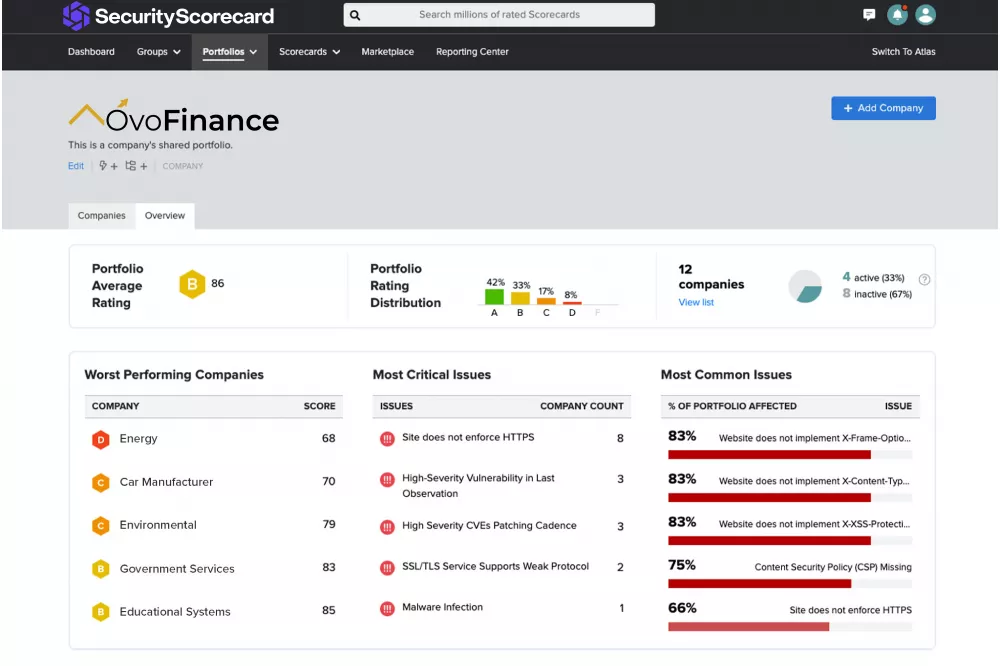
Organizations with an F Rating have a 7.7x higher likelihood of sustaining a breach compared to organizations with an A. Our machine learning-tuned risk factor weights optimize the correlation between our Ratings and relative breach likelihood so you can make smarter business and security decisions.
Improve your security posture with automated and customized remediation plans to achieve a target SecurityScorecard Rating. You’ll see your rating improve as you address key vulnerabilities within your IT infrastructure.
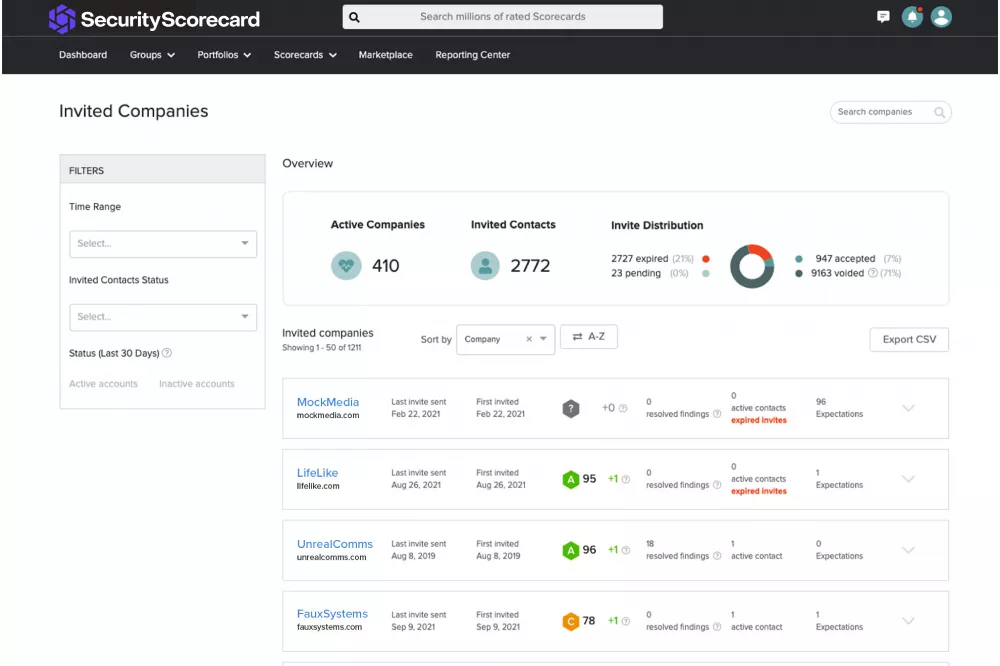
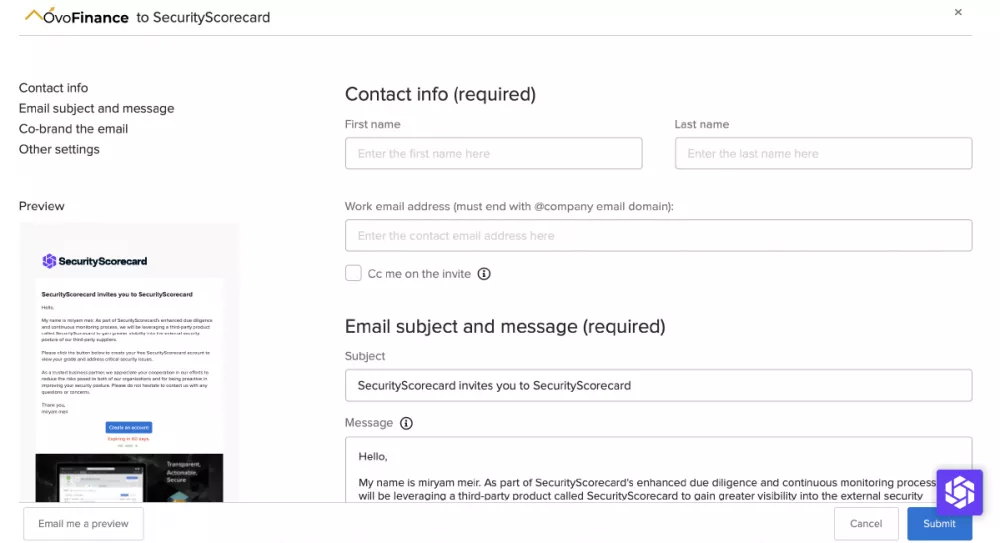
Invite your vendors and business partners to access their Scorecards and remediation plans, so you can build a more resilient ecosystem. On average, rated organizations that are invited to the platform with low security Ratings (C, D, or F) exhibit a 7-to-8 point score improvement within 3 months.
Boost security posture
Continuously monitor the threat landscape, scanning billions of signals each week to help you identify hidden risks so you can take action.
Secure your ecosystem
Enable collaboration between business units, vendor-risk managers (VRMs), and vendors. Shared security goals lead to a safer digital ecosystem for all.
Drive action
SecurityScorecard integrates with dozens of Marketplace partners, turning findings into automated workflows within your tech stack.
Report results
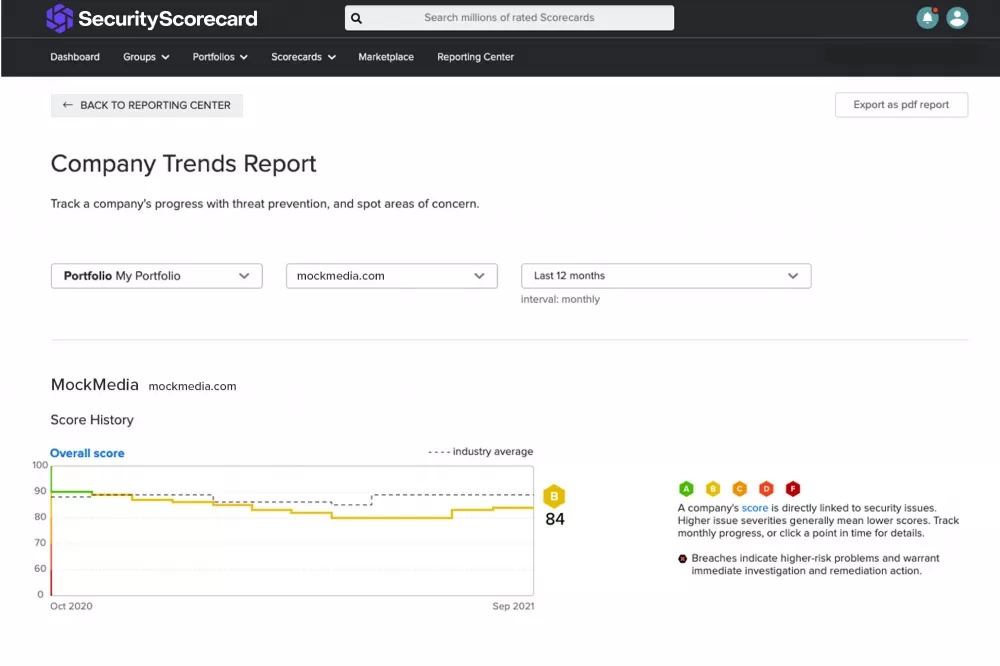
Deliver powerful, automated reports in minutes. Communicate progress to company executives on internal risk management initiatives, or highlight third-party risk trends.
How Can We Help?
Whether you’re ready to speak someone about pricing, want to dive deeper on a specific topic,
or have a problem that you’re not sure we can address, we’ll contact you with someone who can help.
Head Office
1005 Metropolitan Ave, Corner Kakarong, Makati, 1205 Metro Manila
Cebu Office
2F Unit 202-204, GMC Innovation Center, M. J. Cuenco Ave, Brgy San Roque Cebu City 6000
Davao Office
Unit 11, Plug Holdings Bldg, 141 R. Castillo St, Agdao, Davao City, 8000 Davao del Sur

