Understand risk within your IT infrastructure.
In order to truly understand your exposure, you need to obtain an accurate picture of your IT environment. Once you identify your organization’s biggest threats, you can prioritize remediation.
Discover assets
Scan the public IP space daily, ensuring that your asset inventories are both accurate and up to date.
Verify your footprint
Understand why assets are assigned to your organization and quickly refute any inaccuracies.
Move against threats
Leverage automated workflows to be alerted to zero-day incidents and other threats.
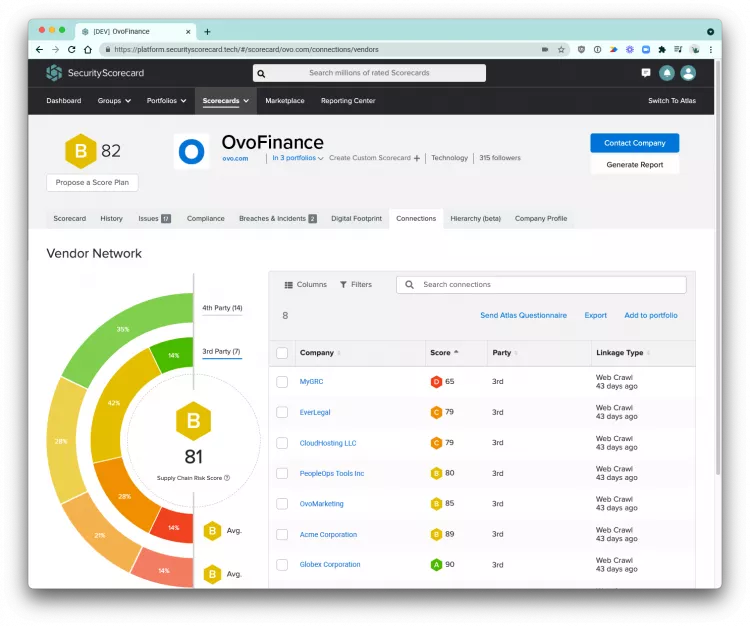
Understand how your Vendors Impact your Security Posture
Your security posture is never just your security posture. It’s a combination of yours, your vendors, and their vendors that make up your entire ecosystem.
Gain a complete view of your vendor ecosystem, the security posture of each vendor, and a private Supply Chain Risk Score to understand the security posture of your entire ecosystem.
- Visualize your full vendor ecosystem: gain a ubiquitous view of cyber risk with unparalleled graphics giving you a full view of your ecosystem risk.
- Drive targeted discussions with your board: pinpoint related risks and specific vulnerabilities within every vendor, so you can partner with your third parties to accelerate risk mitigation.
- Streamline vendor risk management workflows: simplify mitigation and quickly identify threat exposures with a single dashboard highlighting areas of strength and weakness across the full spectrum of vendors–including your fourth-party vendors.
Prioritize action
Sort and filter asset reports to identify the IP’s that have the greatest impact on your rating. SecurityScorecard makes it easy to know which issues to address first.
Uncover shadow IT
Discover endpoints, applications, and web domains that are unknown to your IT and Security teams to prevent shadow IT from becoming a threat.
Accelerate risk mitigation
Strengthen the tools you already have in your stack. With a flexible API and dozens of out-of-the-box integrations, you can trigger automated actions within your existing security tools.
“When I conducted my external vulnerability scan, I had to rely on the information I was given—roughly 200 IP’s. The SecurityScorecard platform showed me that I actually have more than 17,000 digital assets!”
Take a proactive stance to your cybersecurity.
The beginning of your journey to an optimized security posture starts with understanding your security rating. It explains which risk factors need your attention.
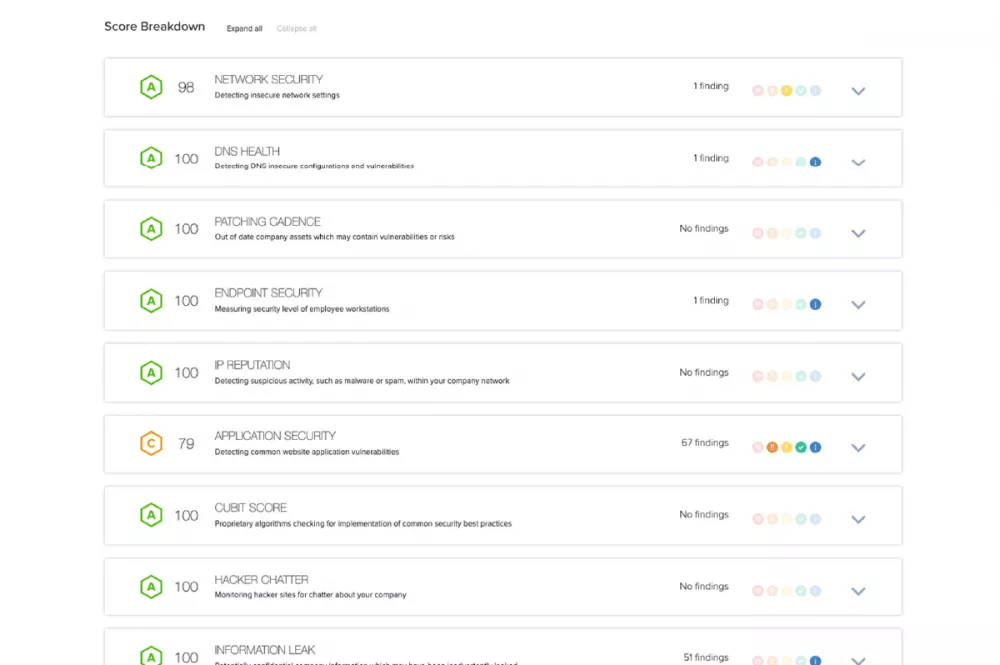
With your scorecard in hand, you can review the attributed assets that make up your digital estate. You’ll be able to identify shadow-IT assets such as unmanaged endpoints, apps, and web domains.
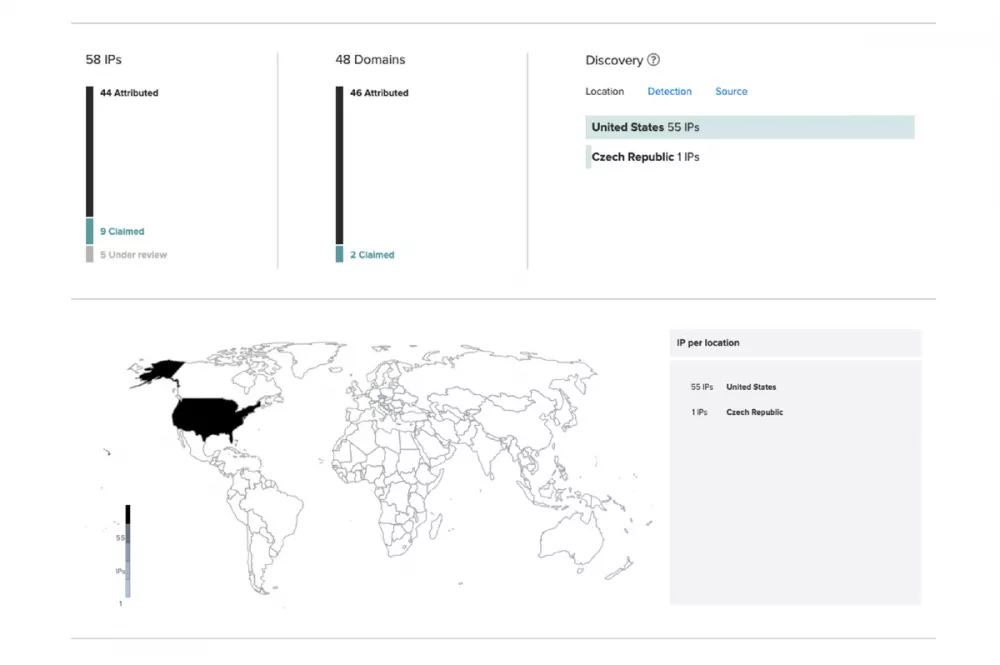
Knowing how your rating compares to others in your industry helps you understand which risk factors are common in your market segment as well as your own organization’s gaps.
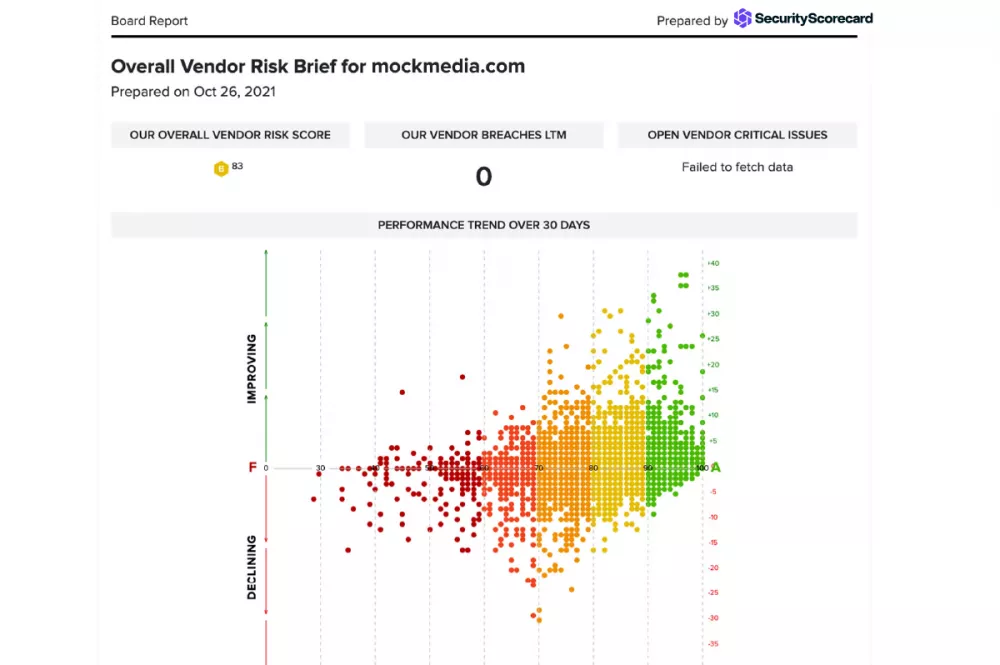
SecurityScorecard integrates with the security tools you already have, making it easy to turn insights into actionable workflows. This allows you to maximize the impact of your security resources and scale your operations.
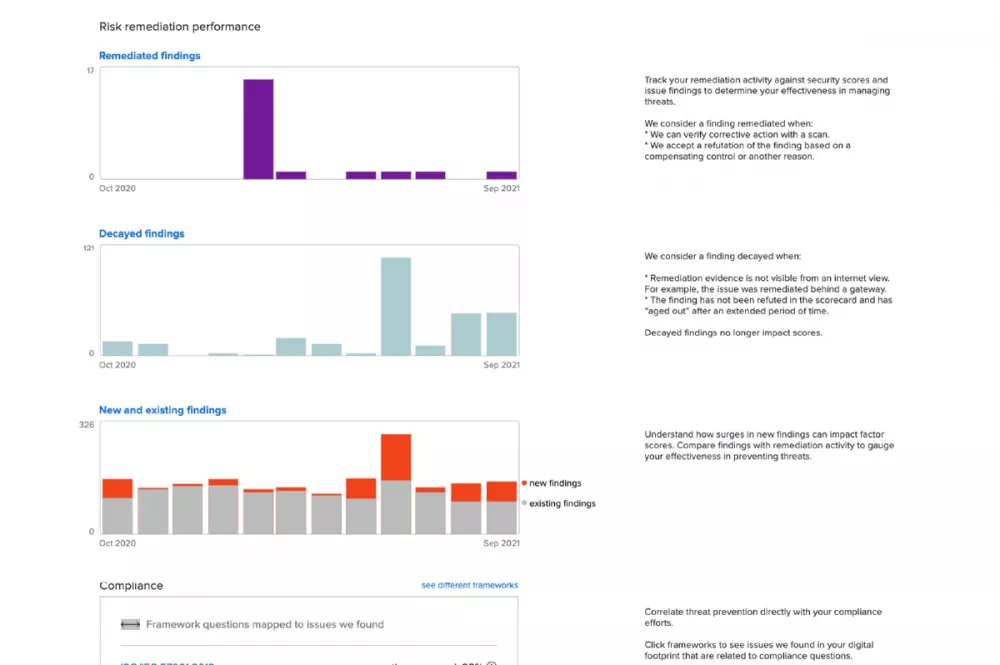
Cyber risk is now a top concern for executives and boards. Report progress on internal initiatives and third-party risk to help executive stakeholders align business and security strategy.
How Can We Help?
Whether you’re ready to speak someone about pricing, want to dive deeper on a specific topic,
or have a problem that you’re not sure we can address, we’ll contact you with someone who can help.
