Using AI to idenfy cybercrime masterminds
Online criminal forums, both on the public internet and on the “dark web” of Tor .onion sites, are a rich resource for threat intelligence researchers. The Sophos Counter Threat Unit (CTU) have a team of darkweb researchers collecng intelligence and interacng with darkweb forums, but combing through these posts is a me consuming and resource-intensive task, and it’s always possible that things are missed.
As we strive to make beer use of AI and data analysis, Sophos AI researcher Francois Labreche, working with Estelle Ruellan of Flare and the Université de Montréal and Masarah Paquet-Clouston of the Université de Montréal, set out to see if they could approach the problem of identifying key actors on the dark web in a more automated way. Their work, originally presented at the 2024 APWG Symposium on Electronic Crime Research, has recently been published as a paper.
The Approach
Researchers adapted a framework by Bouchard and Nguyen, combining it with social network analysis to distinguish professional from amateur cybercriminals. They analyzed 11,558 posts from 4,441 users across 124 e-crime forums (2015 2023), identifying links between CVEs and CAPECs using the Flare search engine.
After filtering out general or non-mappable CVEs, the dataset was refined to 2,321 actors and 263 CAPECs. They built a bimodal network connecting actors to attack patterns, then applied the Leiden algorithm to detect eight distinct “Communities of Interest” based on shared CAPEC focus.
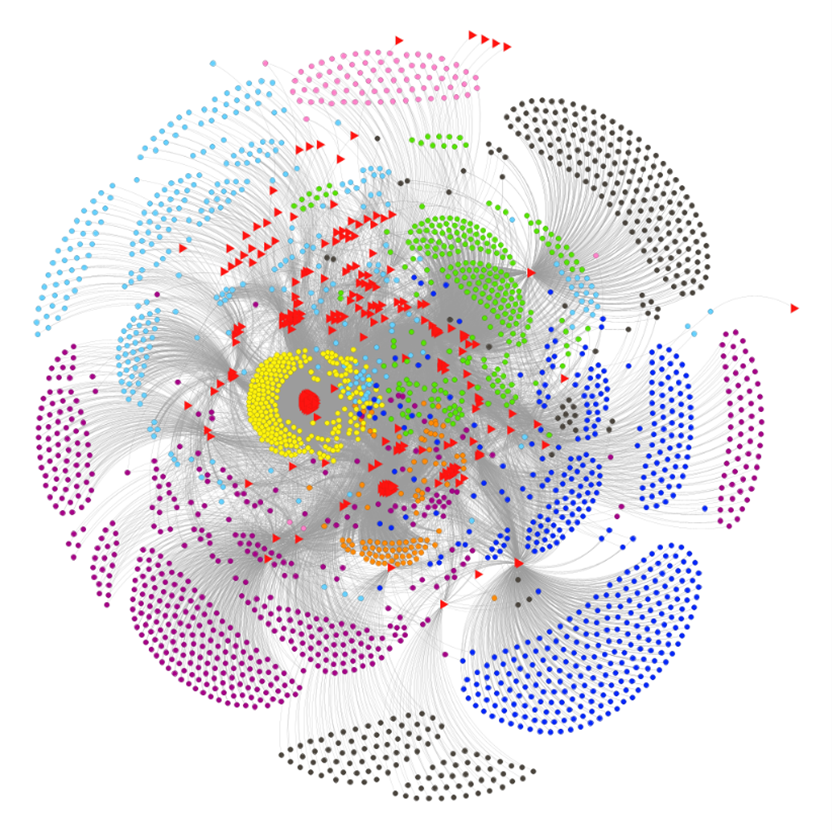
Conclusion
The research process includes defining problems and seeing how various structured approaches might lead to greater insight. Derivatives of the approach described in this research could be used by threat intelligence teams to develop a less biased approach to identifying e-crime masterminds, and Sophos CTU will now start looking at the outputs of this data to see if it can shape or improve our existing human-led research in this area.

