Secure Your Cloud Apps Without Compromising Your Security
Secure corporate data in cloud applications from exfiltration to unauthorized users or devices while keeping your employees productive

Monitor and regulate access to cloud apps
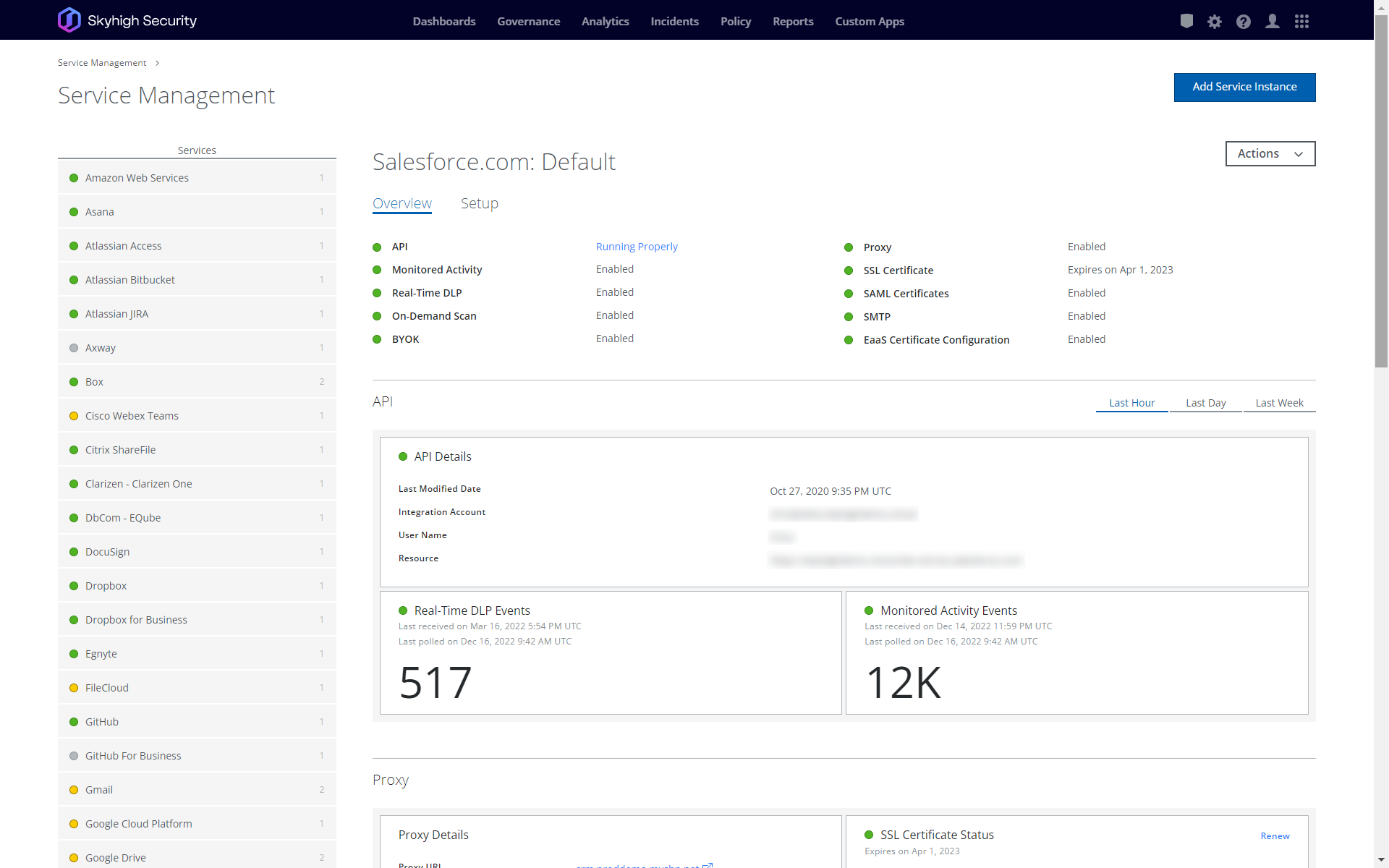
Skyhigh CASB through its inline deployment modes (forward and reverse proxy) enables real-time control over user access to sanctioned and unsanctioned cloud services. No other CASB vendor has matched the comprehensive multi-mode coverage provided by Skyhigh Security.
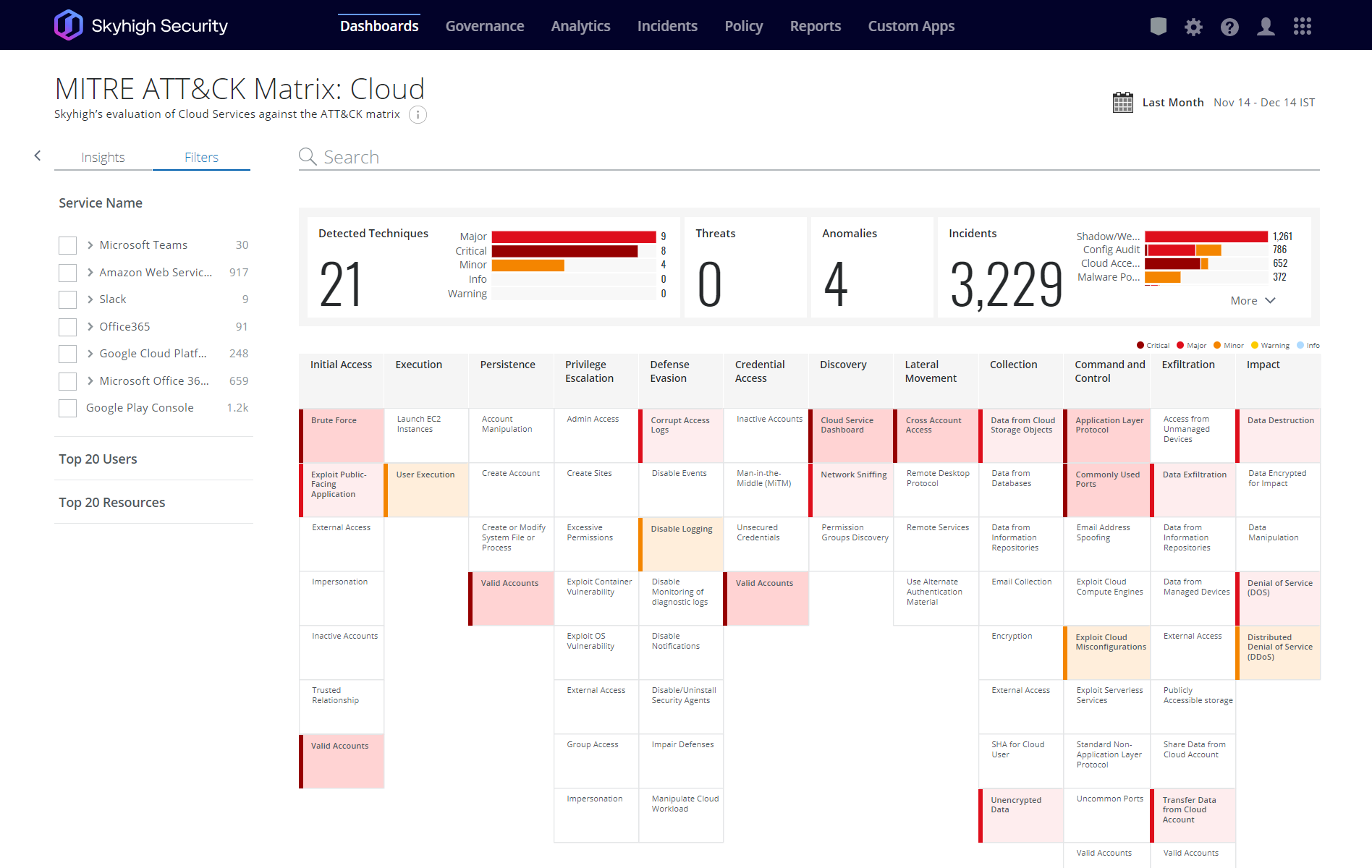
Protect against cloud security threats and misconfigurations
Analyze billions of cloud events with machine learning to detect and mitigate threats occurring throughout your portfolio of cloud services. Reduce the risk of misconfiguration through continuous auditing and automated remediation of detected vulnerabilities. Skyhigh Security is the first CASB vendor to introduce MITRE ATT&CK mapping into the multi-cloud workflow.
What you can expect from Skyhigh CASB

Sensitive Data Discovery
Always know where your data is stored and discover sensitive data at rest within your cloud services. Quickly remediate any content that violates your company policies
Real-time Activity Monitoring Controls
Apply real-time controls to protect your data as user activity occurs, including granular content sharing and access controls

Cloud Registry
Gain access to the world’s largest and most accurate registry of cloud services based on a customizable 261-point risk assessment to support risk-aware cloud governance

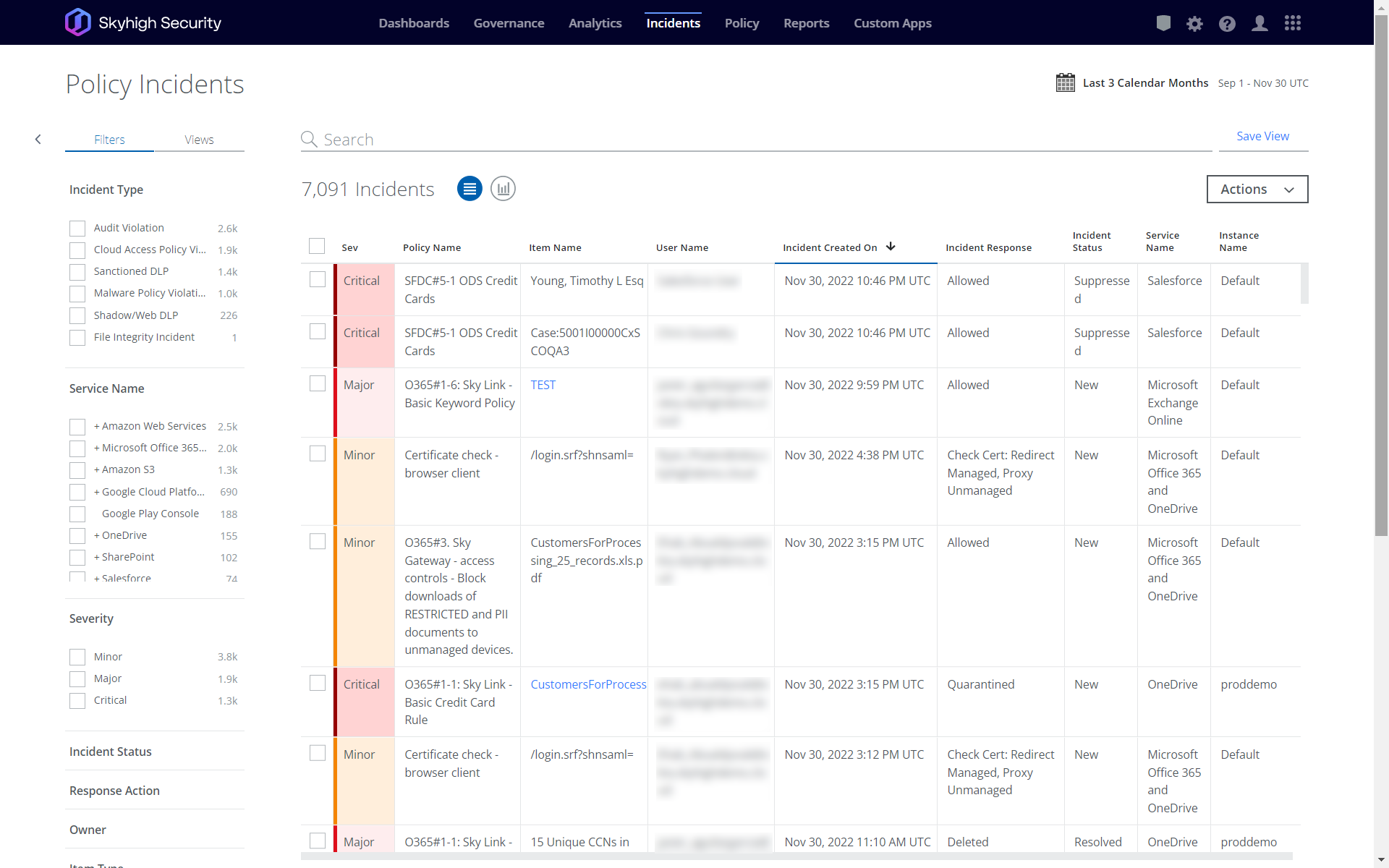
Guided Investigation and Learning
Capture a comprehensive audit trail of all user and administrator activities to support post-incident investigations and forensics

Insider Threat Detection
Leverage machine learning to detect negligent and malicious behaviour including insider threat actor activity

Structured Data Encryption
Protect sensitive, structured data with peer-reviewed, function-preserving encryption schemes using enterprise-controlled keys
How Can We Help?
Inquire now! Fill out the form below and our team will reach out to you as soon as we can.
Head Office
1005 Metropolitan Ave, Corner Kakarong, Makati, 1205 Metro Manila
Cebu Office
2F Unit 202-204, GMC Innovation Center, M. J. Cuenco Ave, Brgy San Roque Cebu City 6000
Davao Office
Unit 11, Plug Holdings Bldg, 141 R. Castillo St, Agdao, Davao City, 8000 Davao del Sur