In an era where cyberattacks grow more sophisticated by the day, businesses of all sizes can no longer afford to take a passive approach to cybersecurity. Sophos’ 2025 Active Adversary Report makes one thing clear: 24/7 monitoring is not only a must – — it can significantly change your company’s outcomes.
Drawing on insights from hundreds of real-world incident response and MDR cases, the report takes an in-depth look at the tactics criminals are deploying in the field and how companies should adjust to keep pace. If the right detection measures were in place, it is evident that many cyberattacks could have been identified early – if the right detection measures were in place. With just three 3 hours between detecting ransomware and data being encrypted, it underscores the growing need for a proactive, offense-minded strategy to keep pace with increasingly sophisticated adversaries.
In this edition, we explore the key findings from the report and what they mean for organizations aiming to stay ahead of modern threats.
1. Ransomware Dominates —– But Early Detection Changes the Game
Ransomware is still the most common cyber threat affecting organizations, showing up in 65% of Sophos Incident Response cases and nearly a third of Managed Detection and Response (MDR) investigations. But the danger goes beyond just locking files. Attackers often begin stealing sensitive data just three days after breaking in. Once this data the begins, companies have a very short window — just 2.7 hours on average — to spot the breach and act before ransomware encrypts their systems and data.
2. Credential Theft Leads the Way
Credential the continues to be the most common entry point for attackers in both MDR and Incident Responses cases we reviewed, with over 41% of incidents involving the use of stolen credentials to simply log in rather than break in. Cyber attackers are still using brute-force tactics, but the most common way they break in is by using stolen passwords (41%) or taking advantage of software weaknesses (22%). Brute-force attacks — where hackers adversaries try many passwords until one works — come in third at 21%, as shown below:
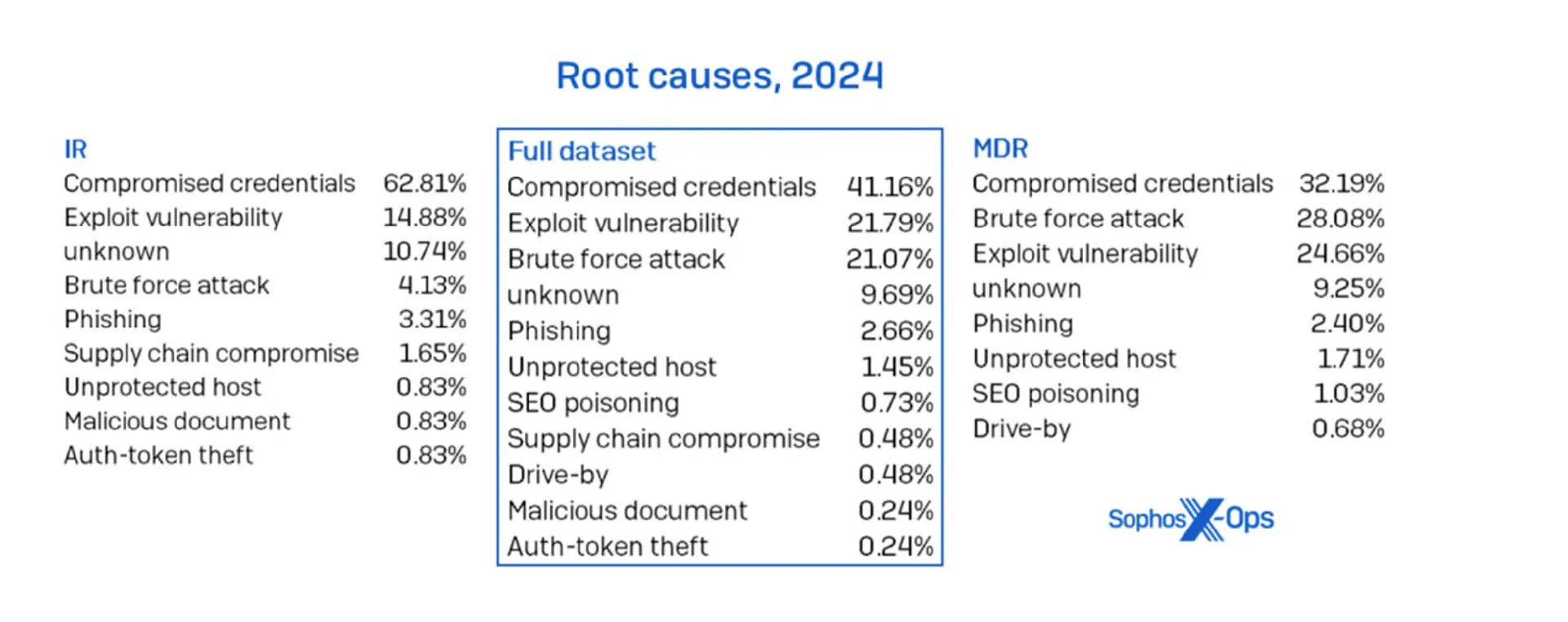
Root cause in 2024 varied between MDR and IR cases, but compromised credentials are still the leading cause of pain in both datasets
This highlights the importance of rapid detection and MDR solutions integrated with services like Office 365, ensuring any malicious login attempts or suspicious activity is alerted in minutes, not hours.
3. Low MFA Adoption Makes It Easy for Attackers to Walk Right In
Weak multifactor authentication (MFA) practices continue to leave organizations exposed, allowing attackers to bypass technical barriers and simply access systems with stolen credentials via remote services. Remote Desktop Protocol (RDP) remains the most frequently abused Microsoft tool, featuring in 84% of attacks in 2024. Ideally, all RDP access should be tightly controlled through both network restrictions and user identity verification. Adding MFA to the authentication process and applying the principle of least privilege significantly reduces risk. However, the availability of MFA across breached organizations is trending in the wrong direction. In 2022, 22% of victims lacked MFA —– that figure nearly tripled to 63% in 2024, underscoring a growing and preventable security gap.
4. The Growing Threat of Remote Ransomware
Some may ask why we’re still seeing ransomware cases at all in an MDR service. One big reason has to do with unprotected systems and their relationship with remote ransomware —– where attackers compromise an unmanaged device and use it to encrypt data on managed, domain-joined machines. Therefore, all malicious activity —– ingress, payload execution and encryption —– occurs on unmanaged machines, therefore bypassing the organization’s security tools. Sophos X-Ops has seen this surge, with cases rising 141% since 2022.
What this means for cybersecurity in 2025
Practitioners, you’re not alone —– and you don’t have to go at it alone.
By leveraging specialized expertise and tools, you can stay ahead of threats instead of just reacting to them. Business and technology leaders, empower your teams: invest in dedicated security resources so your IT staff can focus on supporting the business while experts hunt and neutralize adversaries. When dedicated eyes are watching —– and ready to act –— your defenses become far more resilient.
This marks the fifth year of Sophos’ Active Adversary Report, and it’s also a year of two important firsts. For the first me, the report includes insights not only from our Incident Response cases — where Sophos is brought in during an active attack — but also from our Managed Detection and Response (MDR) service, which continuously protects our MDR customers. Additionally, we’re proud to share our full 2024 dataset publicly for the first me, with the goal of encouraging wider conversations about attacker behavior.
