Effective communication is the backbone of healthcare delivery. As complexity rises and expectations grow, the contact center has evolved from a transactional hub into a strategic asset, managing patient flow, coordinating care, and supporting clinical an ...
Incident Management Retainer Services Catalog Overview
Overview This catalog contains information about the standardized Proactive & Professional Services that are available with the Incident Management Retainer (IMR) through use of Service Units only. This catalog contains a wide range of services th ...
The Future of Authentication in 2026: Yubico Experts on Passkeys, AI & Cyber Resilience
If you’ve followed us and our blog this year, you’ve read various posts from Yubico experts sharing their insights and expertise on the latest trends impacting cybersecurity around the world. We strive to post content that is insightful to not just our cu ...
The Road to cyber resilience: YubiKey partners and integration are cornerstones to phishing resistance in 2026
As generative and agentic AI continue amplifying the rise in phishing attacks globally, credential-based attacks are also evolving and becoming more sophisticated. Heading into a near year faced with new cyber threats and challenges, the need for truly ph ...
JumpCloud’s Acquisition Unlocks Faster, More Secure IT For Global Businesses
For IT teams, the mission is simple. Get your organization connected to the resources they need to get their job done.But making it happen is hard work. How do you securely connect every identity and device to the resources they need? How do you help ever ...
Break Free From the Software Industrial Complex with the Anti-Platform
For decades, the software industrial complex has been selling us the same story: Buy the platform. Bow to the platform. Build everything on the platform.Here’s what they really mean when they say “platform”:Command-and-control over your dataVendor lock-in ...
Couchbase Mobile Delivers Major Advancements for Building Offline-First AI Applications at the Edge
Couchbase is the enterprise grade, cloud to edge developer data platform leading the market in multi-purpose capabilities for building high-scale, AI-powered apps. Mobile is a core strength and strategic focus at Couchbase, far outpacing edge support offe ...
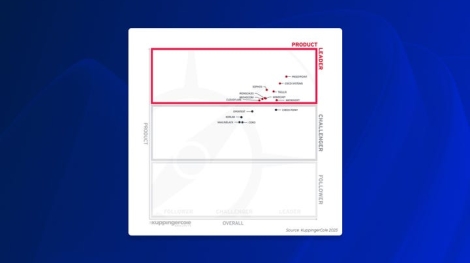
Sophos Named a Leader in the KuppingerCole 2025 Leadership Compass for Email Security
A milestone that reflects our constant progress in email security.We’re excited to announce that Sophos has been named a Leader across all four evaluation categories — Overall, Product, Innovation, and Market — in the 2025 KuppingerCole Leadership Compass ...
Sophos Firewall v22: Your Top-Requested Features
Get involved in the Sophos Firewall v22 Early Access Program today!In the last few articles on the topic of our latest Sophos Firewall release, we’ve discussed many of the important enhancements to Secure by Design in Sophos Firewall v22. You will be deli ...
Defending the Future: Our Commitment to Responsible AI in Cybersecurity
Combining advanced technologies with human expertise to defend against evolving threats.In the rapidly evolving landscape of cyber threats, artificial intelligence is no longer a luxury: it’s a necessity. At Sophos, we recognized this reality early: we’ve ...